THANK YOU FOR SUBSCRIBING

Quad Miners: Evidenced Intelligence

 Bum Joong, Co-Founder & CEO, Jay Kim, Global Sales Director
Bum Joong, Co-Founder & CEO, Jay Kim, Global Sales DirectorWhen flight JT610—a newly commissioned Boeing 737 Max— crashed shortly after takeoff, investigators were left baffled without an answer as to why the mishap occurred. But, upon discovering the black box, a flight data recorder (FDR), the investigators said that the same aircraft had experienced similar problems with an automatic safety system days before the crash. These systems could have been turned off even minutes before the crash to avoid the catastrophe altogether. Such is the utility and versatility of a black box – it sees and knows everything that could happen within the installed system. 4 developers—Quad Miners—have created a Network Blackbox of a similar sort, but with far more capabilities in terms of governing a network or a cloud architecture against threats and malicious behaviour. More importantly, Quad Miners provides evidence. Jay Kim, Global Sales Director at Quad Miners, substantiates, “Most solutions in the market detect threats and malicious behavior, but they do not have the evidence to back it up. We provide them the exact evidence of what’s been taken, what was detected, how it was detected, and what is the flow of operations that occurred on the network? Everything from ‘what came in’ to ‘what went out.’” He adds, “Most companies have a hard time finding the root cause of incidents. With our Network Blackbox, our clients can actually tell who came in, how the person made their way into the network, and what they took.”
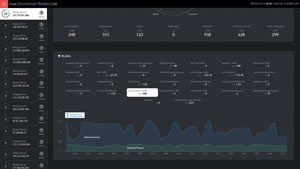
Quad Miners’ Network Blackbox could serve as an all-seeing eye over a network, uncovering the truth that could otherwise be impossible to find. It also guides business leaders in taking definitive action against the threat actors. By utilizing a combination of machine learning, advanced analytics, and signature-based rules to detect anomalous behaviour, Quad Miners informs clients about the severity of incidents, the actual evidence to validate the malicious activities, and the recommendation on a course of action to remediate the incident as quickly and as effectively as possible.
The RootCause Analysis
Security managers, more often than not, struggle to determine if an attack occurred from within the company or outside the company.
With our Network Blackbox, our clients can actually tell you who came in, how the person made their way into the network, and what they took
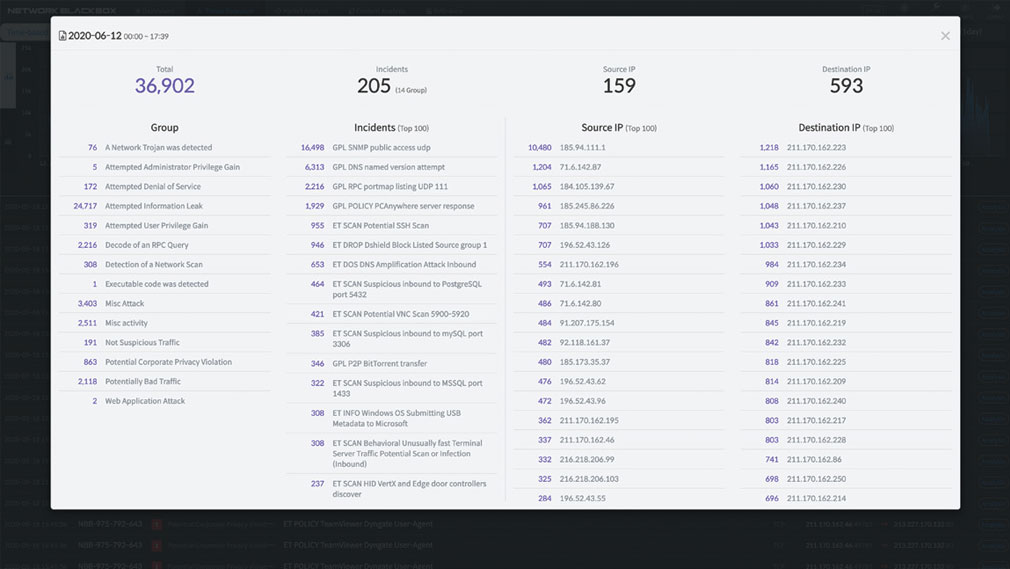
In a day and age where cloud security is still in nascency, with people unclear of what to expect and how to combat threats effectively, a black box that tracks all activities while detecting anomalous activities providers full visibility across the bandwidth, allowing clients to secure business infrastructure and combat threats with greater with efficiency. A use case that substantiates this value proposition is Quad Miners’ recent collaboration with one of the largest enterprises in Korea. Someone inside the client’s organization was leaking confidential information to the company’s competitor. The threat actor was sending small packets of data, translating it into foreign languages. Upon conducting a proof of concept (POC), Quad Miners was tasked to find the culprit. Within a year, Quad Miners was able to show the client the information that was being translated and sent out. Since then, the client has deployed Quad Miners’ solution across various geographical locations such as Vietnam, India, and more.
In another incident, a world-renowned food and beverages outlet had their food ordering application hacked. Since customers were able to load money on to the application and use it to purchase food and drinks at their convenience, the attackers were able to siphon off the cash directly. The organization then employed Quad Miners to determine whom the threat actors were by detecting the IP address that siphoned the money. This evidence-based approach to defending a business infrastructure proves highly beneficial when crimes continue to grow in both uncertainty and sophistication.
Quad Miners has partnered with the likes of IBM, Gartner and more, to study trends in the marketplace, exploring avenues such as the internet of things (IoT), wherein it could understand if someone is trying to establish communication with IoT devices remotely within an office or any controlled environments.
The Story of Four (Quad) Developers
The four developers behind the company’s establishment are symbolized in the name, highlighting their capabilities and ten plus years of experience in their respective fields. Each of the ‘Quad’ developers carries an extensive knowledge base of working with tech giants worldwide, combating security issues of every kind. The ambitious quadruple wanted to incorporate the best of all worlds and the merits of diverse security functionalities into one unified solution that tracks everything that goes through the network and provides evidence of any malicious activity. The company then combined full visibility with an evidence-based approach to safeguarding networks and cloud architectures. By digging deep into packets of information to uncover hidden evidence, a root cause analysis was born through the Network Blackbox solution, laying the foundation to what Quad Miners is today. Since then, Quad Miners has grown by leaps and bounds – the only Korean company to be listed in the Gartner’s Network Detection and Response (NDR) report.
"Rebuilding helps us go back and revisit the network for suspicious activity even during such update patches"
And, the company’s evidence-based approach plays a critical role in achieving this feat. To put things into perspective, despite the existence of firewalls, sophisticated network security solutions, and incident prevention products, organizations require a remediation tool to overcome the crisis, if and when it strikes. “Though there are many threat detection and prevention solutions in existence, once you get hacked, or your network gets breached, you would like to know what was taken, how it was taken, and how to best respond to the issue. And that is precisely what we deliver,” says Kim. In summary, Quad Miners—through its Network Blackbox solution— casts another blanket of security over IT infrastructures, allowing clients to respond immediately and effectively when disaster strikes. More importantly, it reveals how a fundamental breach or infringement was orchestrated, uncovering the footprints of the attackers and the course of action that was unfolded during the incident. This singular truth eliminates uncertainty and actuates a definitive response against any malicious traffic on the network.
The Story of Four (Quad) Developers
The four developers behind the company’s establishment are symbolized in the name, highlighting their capabilities and ten plus years of experience in their respective fields. Each of the ‘Quad’ developers carries an extensive knowledge base of working with tech giants worldwide, combating security issues of every kind. The ambitious quadruple wanted to incorporate the best of all worlds and the merits of diverse security functionalities into one unified solution that tracks everything that goes through the network and provides evidence of any malicious activity. The company then combined full visibility with an evidence-based approach to safeguarding networks and cloud architectures. By digging deep into packets of information to uncover hidden evidence, a root cause analysis was born through the Network Blackbox solution, laying the foundation to what Quad Miners is today. Since then, Quad Miners has grown by leaps and bounds – the only Korean company to be listed in the Gartner’s Network Detection and Response (NDR) report.
"Rebuilding helps us go back and revisit the network for suspicious activity even during such update patches"
And, the company’s evidence-based approach plays a critical role in achieving this feat. To put things into perspective, despite the existence of firewalls, sophisticated network security solutions, and incident prevention products, organizations require a remediation tool to overcome the crisis, if and when it strikes. “Though there are many threat detection and prevention solutions in existence, once you get hacked, or your network gets breached, you would like to know what was taken, how it was taken, and how to best respond to the issue. And that is precisely what we deliver,” says Kim. In summary, Quad Miners—through its Network Blackbox solution— casts another blanket of security over IT infrastructures, allowing clients to respond immediately and effectively when disaster strikes. More importantly, it reveals how a fundamental breach or infringement was orchestrated, uncovering the footprints of the attackers and the course of action that was unfolded during the incident. This singular truth eliminates uncertainty and actuates a definitive response against any malicious traffic on the network.
December 25, 2020

I agree We use cookies on this website to enhance your user experience. By clicking any link on this page you are giving your consent for us to set cookies. More info













